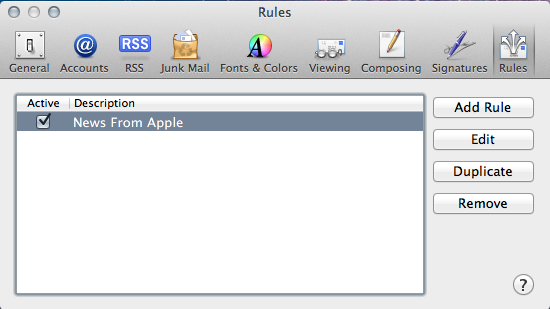
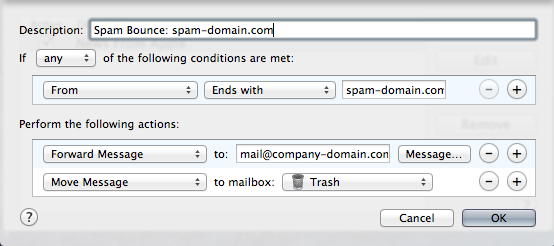
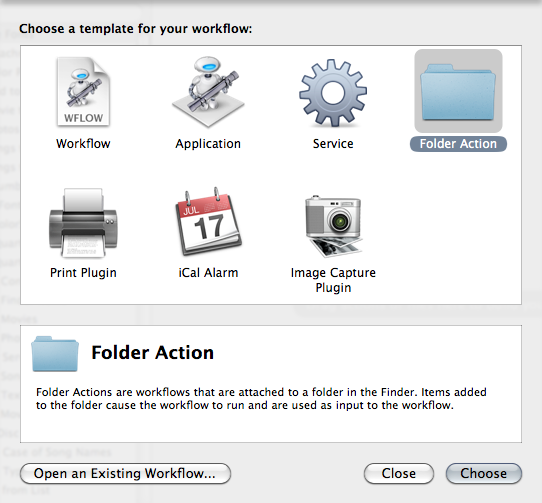
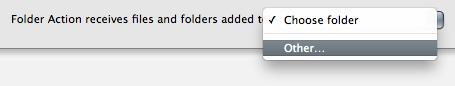
note: if you haven’t watched the Zeitgeist documentaries or aren’t aware of the conundrums it addresses, you should watch at least ‘Zeitgeist Addendum‘ before reading on.
Ideas, suggestions and opinions presented in this article aren’t necessarily the views of the Zeitgeist movement. The article isn’t meant to attack anyone, nor does it mean to offend anyone. It simply reflects the thoughts of the author, as to how a resource-based economy could be introduced — inevitably, this does require some strategic action, that could be understood as conspiracy or the likes, which it is not.
As an avid member of the Zeitgeist movement, I have been pondering possible solutions. What would make an ideal first step toward a resource-based economy (RBE)? I’ll put forth some suggestions, but no definite solution, and I’d love to hear your opinion and suggestions as well.
We are all dependent on the established monetary system, so we cannot simply deny participating in it. It seems almost impossible to fight a system which you are a part of and dependent on. You can of course raise your hand and state your case, but the only ones that can actually make changes to the system doesn’t feel the effects of its flaws, so they have no reason to do so — some may even see it as absurd and will disregard the issue, simply because they already have what they need.
Are we just going to give up then?
Certainly not, we just need to devise an approach which introduces the concept to people unaware of the issue it attempts to resolve, in such a way that it appeals to them. It would be a long hard road, if we are to convince all governments, companies, etc. that we need to make a move into resource-based economy — I’m sure the banks and wealthy people would object to this. So let’s focus on a more strategic method. As a programmer, I like solving problems, it’s pretty much what programming is all about. Programmers design and build systems from the ground up, but some also do the opposite of that — hacking. Hackers take systems apart, learn how it works and make it do things it isn’t supposed to do. What I am getting at is that a hacker’s approach would be the most efficient way of tackling the problem — break the system where it is most vulnerable and exploit it.
Alright, so how do we do that?
Let’s say we were to analyze the monetary-system, and we are looking for vulnerabilities. We need to make sure of a few things when choosing the vulnerability and exploit;
- Nobody should suffer financially from the ‘attack’ — you cannot change the system suddenly like that.
Taking these things into account, we look at the most vulnerable part of the monetary-system, the consumption cycle. This is the three-part wheel that makes the whole system work; the consumer, employee and employer. We know that we cannot have one of these fail completely, but we can weaken its life-blood, money. Money and resources are exchanged in this cycle, and if money were to be slowly phased out of the equation, you’d be left with resource exchange only — this is the ultimate goal, right? Right. What we need now is, citing The Godfather; “an offer you can’t refuse”.
Employers will be the tool of the exploit and the consumer will be the target. The concept needs to be derived from something they are familiar and comfortable with, and that presents a good deal for any person looking to acquire something. This is very familiar ground for most consumers; whether you are buying groceries in the mall or looking to buy a laptop computer, you are looking for the best deal available.
We have the best deal, for anyone — ever!
Since the consumer is always looking for the best deal, supporters of a move toward a resource-based economy would be able to take advantage of the system in a way that not only cripples it, but also exposes how irrelevant money really is — thus if followed through, not only introduces the idea to the public, but proves its function and allow for comparison with the monetary-system. The general purpose of this is to gain trust in the proposed RBE-system by way of example, and make it difficult for monetary-based companies to compete.
The following would require a group of creative individuals, developers, and the likes — people who enjoy creating something out of nothing, not needing to charge money for what they do. Just to clarify, I would volunteer to this group myself. This group will “sell” its products with a set conditions, which allows for both systems to operate on, but promotes the RBE-system. Of course, the exact declaration and definition these conditions would have to be discussed among those who are in favor of taking action on this approach, but this is a rough outline of what I’m thinking it could sound like;
Products are given free of charge if;
- You are RBE-supporting company — this means you offer some or all of your product resources with this same license.
- You need it for any reason other than commercial (eg. study, research, etc.) — this means you do not seek monetary gain from usage of this product.
Should you not meet any of the above, you are subject to pay for the service or product. — Any payments under this license goes mainly to sustain the product and its vendor as long as the monetary-system is in effect and to help RBE develop further.
What good does this do?
Marketing with this ‘licence’ would effectively pull money out of the supply from those who seek monetary gain from their products, and makes the RBE model compete directly with the monetary-system. Granted, the idea is a bit sketchy at this point, and a whole concept on this idea would be a very long article, so has of course been made quite a bit simpler.
Your move!
If you are like me, creating stuff all the time anyway, why not jump in and let’s have a go at it? Although I am studying at this time, and may not have a whole lot of time to develop products, I do want to see any idea through if the community agrees that it could yield results. Have your say, I leave the word up to you!
Read the rest of this entry »
0.000000
0.000000